
In the modern day and age of IoT where the vast majority of human transactions is more and more explicitly done via information and communications technologies (ICT), there is an overwhelming rise in the security risk that comes as a consequence of this need and modernization. This risk is of course much more severe when it involves sensitive information like banking, but even more so when such a potential security compromise can lead up to actual physical/health risk i.e. A Denial of Service caused in the infrastructure of a healthcare organization can actually lead to severe human physical/health risk. As such, strengthening infrastructure & data security in healthcare organizations is deemed as an extremely crucial need and priority in the IoT ecosystem.
To picture the exposure of the Healthcare sector to cyberattacks and risks, according to a recent survey of healthcare providers, 39% of healthcare organizations suffered ransomware attacks already in 2020[1]. More specifically, 44% of healthcare providers suffered a phishing attack, 39% were the victims of ransomware and 35% were hit by data theft by insiders.
This vulnerability of healthcare organizations worldwide is even more enlarged by other unique factors like
- Shortage of cybersecurity expertise in healthcare due to the antagonistic salaries and benefits in other industries
- Outdated operating systems, computers, applications, and devices
- New risks deriving from the application of Telehealth practices
- Etc.
The complexity of the infrastructure and services found in the healthcare sector, i.e., a hospital, with multiple departments and entities, demands a versatile monitoring system able to collect and analyze data deriving from multiple sources in real-time, as well as correlate the vast amount of security-related data.
This need can be met using a Security Information and Event Management (SIEM) system. These systems are well-established security solutions that allow organizations to efficiently collect and analyse log data from various digital devices, identifying potential security threats and vulnerabilities. Specifically, in the Healthcare sector, the SIEM solutions give organizations a full view of their security events to detect cyberattacks that can threaten not only patient data but also a hospital’s services.
In the HEIR project, where a thorough scientific investigation is conducted for real-time threat hunting services supporting the identification of the most common threats in electronic medical systems, such a solution brings the ability to efficiently deal with cyberattacks that can disrupt Healthcare IT (HIT) infrastructure. In particular, the HEIR SIEM component supplies various security-related data from endpoints of the HIT to the HEIR Interactive Forensics Module[2] and supports the Vulnerability Assessment Module[3] (the HEIR module for the identification of missing updates and/or patches in the HIT infrastructure), providing another source of security information that can be evaluated and exploited together with the rest of the available components and data sources. The HEIR SIEM is based on an open source and enterprise-ready security monitoring solution for threat detection, integrity monitoring, incident response, and compliance, Wazuh[4], which provides a multitude of security-related services that continuously monitor a HIT infrastructure. All data is collected by installed lightweight agents on the monitored devices of a HIT infrastructure, collecting events, and forwarding them to the Wazuh Manager, where data is aggregated, analysed, indexed, and stored. This ensures that the resources needed at the client level are kept to a minimum since the security intelligence and data analysis are solely performed at the server level.
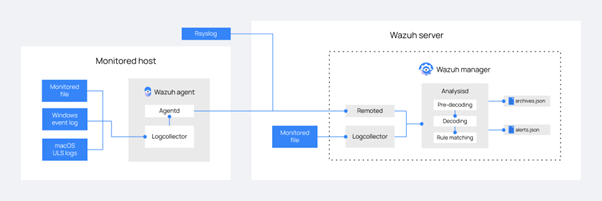
Wazuh clients run on many different platforms, including Windows, Linux, Mac OS X, AIX, Solaris, and HP-UX. The events reported by the Wazuh agents are the outcome of a wide range of tasks such as:
• Inventory of running processes and installed applications
• Log and events data collection
• File and registry keys integrity monitoring
• Monitoring of open ports and network configuration
• Configuration assessment and policy monitoring
These events are received by the Wazuh server and processed through a toolset of decoders and rules, using threat intelligence to look for well-known Indicators of Compromise (IOCs). As a result of this analysis, all events are appointed a severity level enabling the administrators to focus on the crucial issues that need to be addressed. This is further delivered via customized alerts that are sent to an Elastic Stack[5] which also provides a powerful interface for data visualization and analysis via its integration with Kibana. In addition to logs and events deriving from the operating system, Wazuh can collect and integrate logs deriving from network devices such as routers, firewalls, etc. either by monitoring the log files themselves or via forwarding log messages. This can potentially facilitate the collection of logs from medical devices that needs to be monitored within the hospital use-case environments. Furthermore, Wazuh offers a powerful application programming interface (RESTful API) that allows the interaction of the Wazuh manager with web browsers, command line tools like cURL[6], or any scripts or programs that can make web requests. This, combined with the RESTful APIs provided by ElasticSearch, will greatly aid the seamless accumulation of the HEIR SIEM security metrics in the integrated HEIR Client and its role in the RAMA score calculation.
Furthermore, the use of the ITML’s software product, Security Infusion as the basis of the Heir environment in all of the pilots, aids in the seamless deployment and integration of all the developed HEIR components by providing, apart from Wazuh, - a set of much-needed tools such as:
- distributed, free and open search and analytics engine for all types of data, including textual, numerical, geospatial, structured, and unstructured (Elastic Search)
- the means to enable applications, systems, and services to communicate with each other and exchange information via a message broker (Kafka)
- Kubernetes, also known as K8s, is an open-source system for automating the deployment, scaling, and management of containerized applications.
- Etc.
It should also be noted that the verbose functionality and abilities of Wazuh are further complemented by the parallel use of the deployed Security Infusion agents (https://security-infusion.com), enabling the collection of extra metrics like Resource Allocation (CPU/Memory/Disk) analysis of computer processes, open file handles, etc. This provides an even more verbose real-time monitoring of the computer endpoints and additionally provides valuable data to be used post-event for forensic purposes.
Taking into consideration the HEIR SIEM technology, its main role is to provide via Elastic all the necessary information collected from the monitored devices of the HIT infrastructure to a dashboard, namely Forensics Visualization Toolkit (FVT)[7][8], that provides to its users a timeline-based representation of the security events captured. Data deriving from the SIEM agents are presently explicitly portrayed on the FVT serving as a GUI for the threat hunting module for use by the hospital IT administrators.
During the demonstration and validation phase of the HEIR project, the SIEM module will be evaluated in real-world use case scenarios and will be showcased in its interaction with the rest modules of the HEIR framework. Responsible for providing and deploying the SIEM technology in the project is ITML which acts as the system integrator and leader of the WP5 of the HEIR project.
[1] https://www.netwrix.com/download/documents/2021_Netwrix_CDSR_Healthcare.pdf
[2] HEIR D2.2 – The HEIR facilitators package: 1st complete version (public) - https://heir2020.eu/sites/default/files/docs/HEIR_D2.2_Facilitators-V1_v1.0.pdf
[3] HEIR D2.2 – The HEIR facilitators package: 1st complete version (public) - https://heir2020.eu/sites/default/files/docs/HEIR_D2.2_Facilitators-V1_v1.0.pdf
[5] https://www.elastic.co/elastic-stack
[7] HEIR D2.1 - The HEIR facilitators package MVP (public) - https://heir2020.eu/sites/default/files/docs/HEIR_D2.1_HEIR-facilitators-package-MVP_V1.0.pdf
[8] HEIR D2.2 - The HEIR facilitators package 1st complete version (public) – https://heir2020.eu/sites/default/files/docs/HEIR_D2.2_Facilitators-V1_v1.0.pdf
